Digital Identity & Cybersecurity: What You Need to Know in 2025
Digital Identity & Cybersecurity: What You Need to Know in 2025 sets the stage for a deep dive into the world of cybersecurity, shedding light on the crucial aspects that will shape the digital landscape in the coming years.
Delve into the intricacies of evolving threats, emerging technologies, and data protection to equip yourself with the knowledge needed to navigate the cyber realm with confidence.
Overview of Digital Identity & Cybersecurity
In 2025, digital identity plays a crucial role in our daily lives as we rely more on online platforms for various activities such as banking, shopping, and social interactions. Digital identity refers to the information that uniquely identifies an individual online, including personal data, login credentials, and online behavior.
Significance of Digital Identity in 2025
Digital identity is significant in 2025 as it enables seamless access to online services, facilitates personalized experiences, and enhances security measures. With the increasing digital footprint, protecting and managing digital identities has become a top priority for individuals, businesses, and governments.
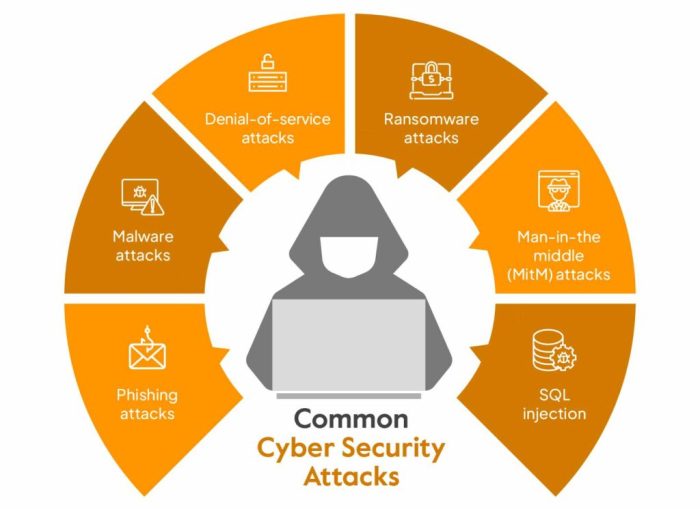
Key Challenges in Cybersecurity
- Ransomware Attacks: Cybercriminals are increasingly targeting organizations with ransomware attacks, encrypting their data and demanding ransom payments.
- Phishing Scams: Phishing scams continue to evolve, with attackers using sophisticated tactics to trick individuals into revealing sensitive information.
- IoT Vulnerabilities: The proliferation of Internet of Things (IoT) devices has created new security vulnerabilities, making it challenging to secure connected devices.
- Data Breaches: Data breaches are on the rise, exposing sensitive information such as personal data, financial details, and intellectual property.
Evolving Landscape of Cybersecurity Threats
- AI-Powered Attacks: Cyber attackers are leveraging artificial intelligence (AI) to launch more targeted and sophisticated attacks.
- Supply Chain Vulnerabilities: Supply chain attacks have become a significant concern, as cybercriminals target third-party vendors to gain access to larger organizations.
- Zero-Day Exploits: Zero-day exploits, which target previously unknown vulnerabilities, pose a significant threat to organizations as they have limited time to patch or mitigate the risks.
Emerging Technologies in Cybersecurity
As technology continues to advance, new tools and strategies are being developed to combat cyber threats. Let's explore some of the emerging technologies shaping the future of cybersecurity.
AI and Machine Learning in Cybersecurity
Artificial Intelligence (AI) and Machine Learning have revolutionized cybersecurity practices by enabling systems to detect and respond to threats in real-time. These technologies can analyze vast amounts of data to identify patterns and anomalies, helping to enhance threat detection and response capabilities.
Role of Blockchain in Digital Identity Security
Blockchain technology provides a decentralized and secure way to manage digital identities. By storing identity data in a tamper-proof and transparent manner, blockchain enhances security and privacy, reducing the risk of identity theft and fraud.
Impact of IoT Devices on Cybersecurity Measures
The proliferation of Internet of Things (IoT) devices has expanded the attack surface for cybercriminals, posing new challenges for cybersecurity. Securing IoT devices is crucial to prevent unauthorized access and protect sensitive information, requiring innovative solutions to safeguard interconnected systems.
Privacy and Data Protection
In the digital age, privacy and data protection have become crucial aspects of safeguarding individuals' digital identities and sensitive information.
Importance of Data Privacy Regulations
Data privacy regulations play a vital role in protecting individuals' personal information from unauthorized access and misuse. Regulations such as the GDPR (General Data Protection Regulation) in the European Union and the CCPA (California Consumer Privacy Act) in the United States set guidelines for how organizations collect, process, and store personal data.
Compliance with these regulations helps in building trust with customers and ensures that their data is handled responsibly.
Role of Encryption in Data Protection
Encryption is a key technology in protecting sensitive information from cyber threats. By converting data into a coded format that can only be accessed with the right decryption key, encryption ensures that even if data is intercepted, it remains unreadable and secure.
End-to-end encryption, in particular, is essential for secure communication channels, such as messaging apps and online transactions, where privacy is paramount.
Ethical Considerations in Data Collection and Storage
Ethical considerations surrounding data collection and storage revolve around transparency, consent, and accountability. Organizations collecting data must be transparent about the purpose of data collection and obtain explicit consent from individuals. Additionally, they must ensure that data is stored securely and only used for the intended purposes.
Ethical data practices are essential to maintain trust and respect individuals' privacy rights in the digital realm.
Biometric Authentication and Multi-factor Authentication

Biometric authentication methods, such as fingerprint, facial recognition, and iris scanning, have revolutionized the way we verify our identities in the digital world. These methods rely on unique physical characteristics to grant access to devices or systems, offering a more secure and convenient alternative to traditional passwords.
Biometric Authentication Methods
- Fingerprint: This method involves scanning an individual's fingerprint to match it with a stored template. Fingerprint authentication is widely used in smartphones and laptops for quick and secure access.
- Facial Recognition: Facial recognition technology analyzes facial features to verify a person's identity. It is commonly used in airports, border control, and smartphones for authentication purposes.
- Iris Scanning: Iris scanning captures the unique patterns in an individual's iris to grant access. This method is known for its high level of accuracy and is used in high-security environments.
Benefits of Multi-factor Authentication
Multi-factor authentication (MFA) provides an additional layer of security by requiring users to present two or more forms of verification before granting access. The benefits of MFA include:
- Enhanced Security: MFA reduces the risk of unauthorized access by adding multiple layers of authentication.
- Protection Against Phishing: MFA makes it harder for cybercriminals to gain unauthorized access through phishing attacks.
- User Convenience: While adding an extra step, MFA ultimately enhances user security without compromising usability.
Future Trends in Authentication Methods
With the continuous evolution of technology, the future of authentication methods in cybersecurity is likely to include:
- Behavioral Biometrics: Utilizing unique behavioral traits, such as typing speed or mouse movements, for authentication purposes.
- Continuous Authentication: Implementing authentication measures that continuously verify a user's identity throughout their interaction with a system.
- Blockchain-based Authentication: Leveraging blockchain technology to enhance the security and integrity of authentication processes.
Cybersecurity Training and Awareness
In today's digital age, cybersecurity threats are constantly evolving, making it crucial for organizations to prioritize cybersecurity training and awareness programs. These initiatives help employees understand the importance of cybersecurity and how to protect sensitive information from cyber attacks.
Significance of Cybersecurity Awareness Programs
Cybersecurity awareness programs play a vital role in educating employees about the various cyber threats they may encounter. By raising awareness, organizations can empower their employees to recognize and respond to potential security risks effectively.
- Regularly conducting phishing simulations to test employees' ability to identify suspicious emails and links.
- Providing training on best practices for creating strong passwords and safeguarding sensitive data.
- Organizing workshops or webinars to educate employees on the latest cybersecurity trends and threats.
Common Social Engineering Tactics and Prevention Strategies
Social engineering tactics, such as phishing and pretexting, are commonly used by cybercriminals to manipulate individuals into divulging confidential information. It is essential for employees to be aware of these tactics and how to prevent falling victim to them.
- Phishing:Cybercriminals often send fraudulent emails impersonating legitimate entities to trick individuals into revealing personal or financial information. Employees should verify the sender's email address and avoid clicking on suspicious links or attachments.
- Pretexting:This tactic involves creating a fabricated scenario to extract sensitive information from individuals. Employees should be cautious when sharing personal or company-related details with unknown parties, especially over the phone or email.
- Training and Awareness:Continuous cybersecurity training can help employees stay informed about the latest social engineering tactics and how to identify and report suspicious activities.
Importance of Continuous Cybersecurity Training for Employees
Cyber threats are constantly evolving, making it essential for organizations to provide ongoing cybersecurity training for their employees. Regular training sessions can help reinforce cybersecurity best practices and ensure that employees remain vigilant against potential security breaches.
- Offering specialized training on emerging cybersecurity trends and technologies to equip employees with the knowledge and skills to protect sensitive data.
- Encouraging employees to report any unusual or suspicious activities promptly to the IT department for further investigation.
- Conducting regular security awareness workshops to educate employees on the importance of maintaining a strong security posture both at work and home.
Epilogue
As we wrap up our exploration of Digital Identity & Cybersecurity: What You Need to Know in 2025, remember that staying informed and proactive is key to safeguarding your digital presence in an ever-changing environment.
Expert Answers
How can I enhance my digital identity security in 2025?
In 2025, focus on using advanced authentication methods like biometrics, regularly updating security software, and being cautious with sharing personal information online to enhance your digital identity security.
What are the key challenges in cybersecurity for the upcoming years?
Some key challenges include dealing with increasingly sophisticated cyber threats, ensuring compliance with evolving data privacy regulations, and addressing the security risks posed by emerging technologies like IoT devices.
Why is continuous cybersecurity training important for employees?
Continuous cybersecurity training is crucial to keep employees informed about the latest threats, best practices, and security protocols, empowering them to contribute effectively to the overall security posture of the organization.